AVM Stealer 2026 – Advanced Infostealer Threat Analysis & Protection Guide
Introduction
AVM Stealer 2026 is being discussed in cybersecurity circles as a next-generation infostealer threat designed to target sensitive user data, including browser credentials, cryptocurrency wallets, and communication platforms.
This article provides a high-level security analysis of how such threats operate, the risks they pose, and—most importantly—how users and organizations can defend themselves.
⚠️ This content is for educational and defensive awareness only.
What Is AVM Stealer 2026?
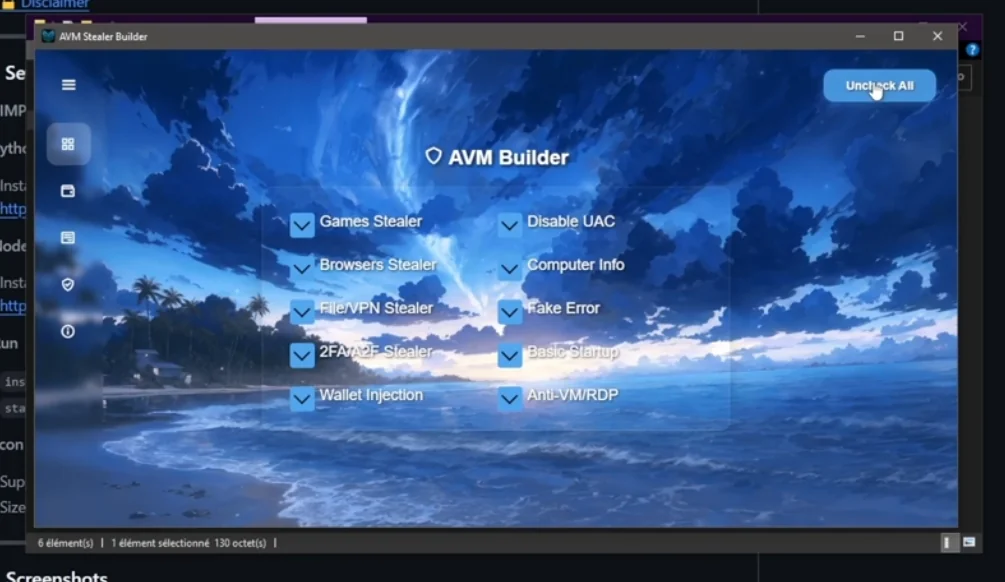
AVM Stealer 2026 is categorized as an information-stealing malware (infostealer). Threats in this class are engineered to silently extract personal and financial data from infected systems and transmit it to remote servers controlled by attackers.
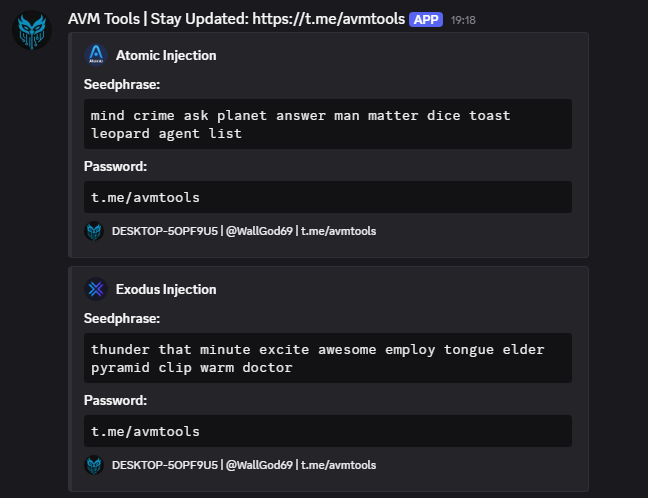
Modern infostealers focus on:
- Stealth
- Speed
- Bypassing traditional security tools
High-Level Threat Capabilities (Security Perspective)
1. Data Targeting Scope
Security researchers note that malware similar to AVM Stealer 2026 often targets:
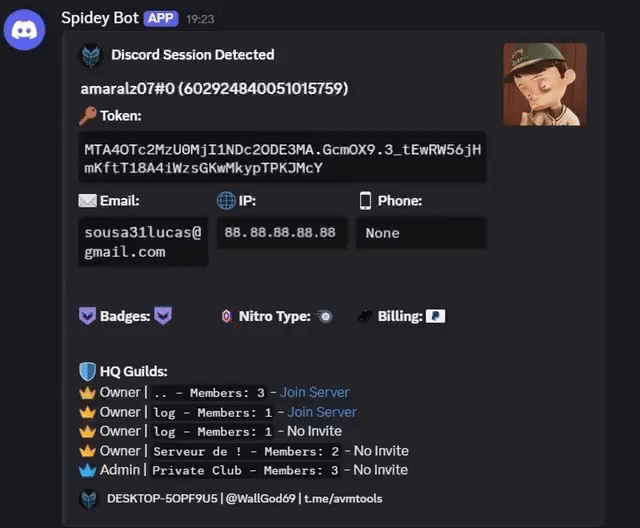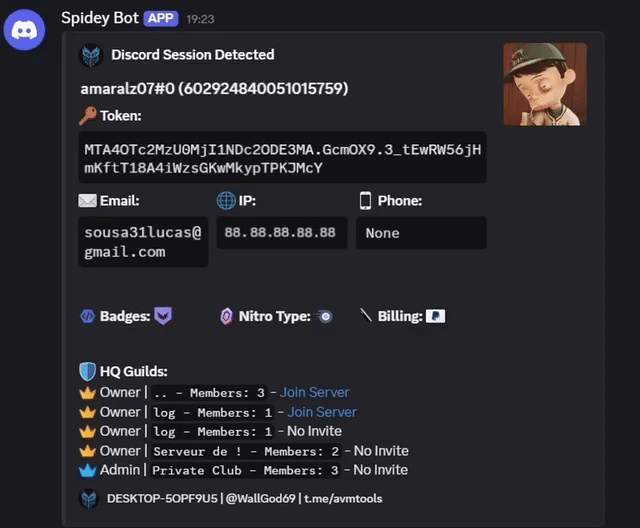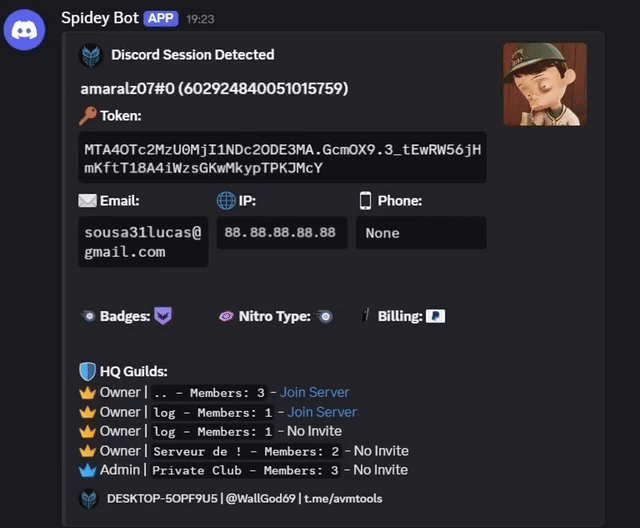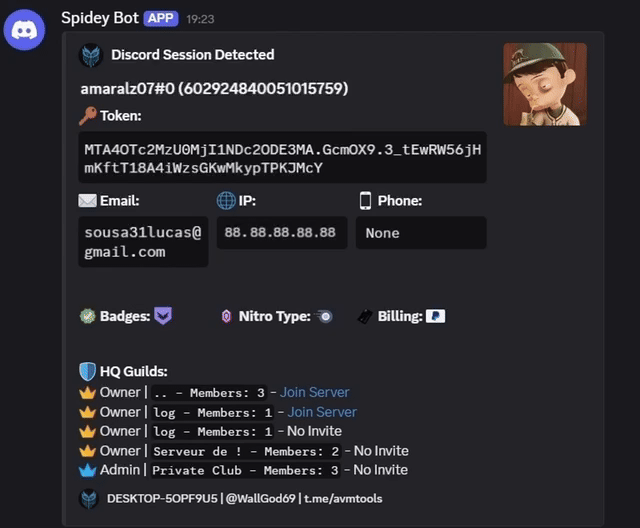
- Browser data (saved passwords, cookies, autofill)
- Cryptocurrency wallets (seed phrases & extensions)
- Messaging platforms (session tokens & local data)
- Gaming platforms (account credentials)
- Clipboard and screen activity
This makes such threats especially dangerous for crypto users and online traders.
2. Stealth & Evasion Techniques
Advanced infostealers rely on anti-analysis mechanisms, including:
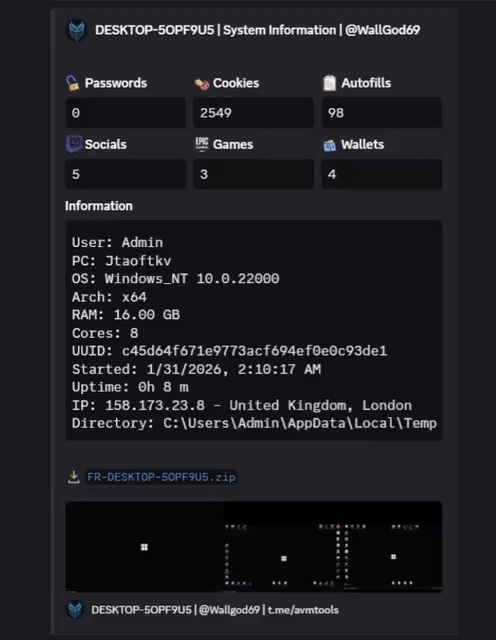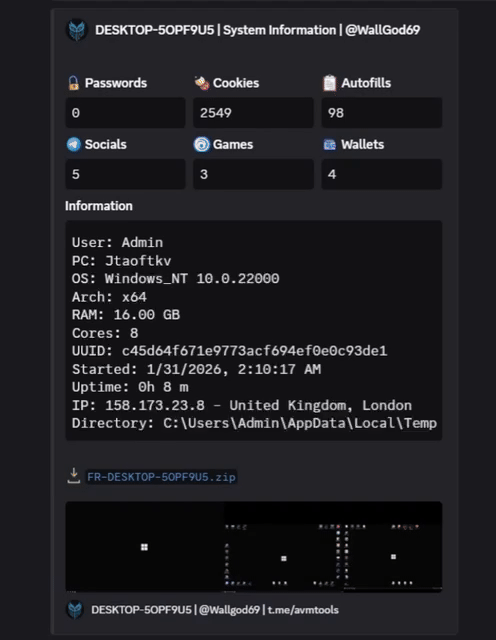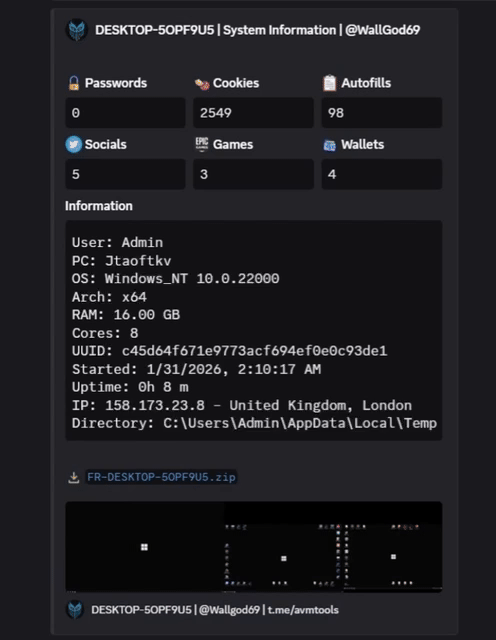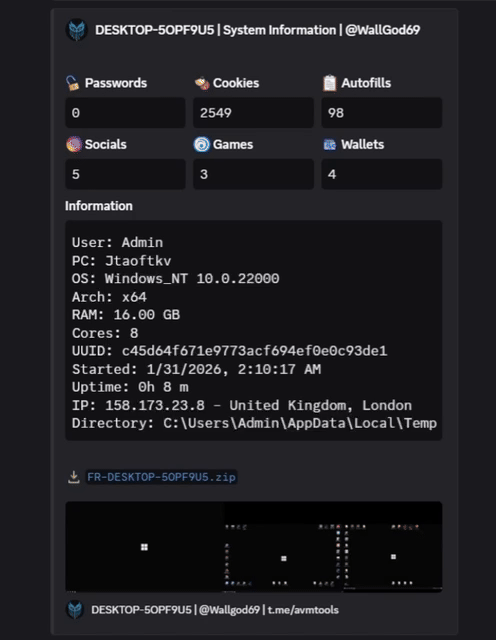
- Hidden execution without visible windows
- Masquerading as legitimate system processes
- Virtual machine and sandbox detection
- Anti-debugging techniques
These methods are designed to delay detection, increasing potential data loss.
3. Data Exfiltration Methods
From a defensive standpoint, malware like AVM Stealer 2026 may use:
- Encrypted outbound traffic
- Webhooks or bot-based communication
- Secure third-party upload services
This allows attackers to receive stolen data in near real time.
Why AVM Stealer-Type Threats Are Dangerous in 2026
The growing adoption of:
- Browser-based wallets
- Cloud password managers
- Messaging apps for business
means a single infection can lead to:
- Account takeovers
- Crypto theft
- Identity fraud
- Long-term privacy compromise
How to Protect Yourself from AVM Stealer 2026
Best Security Practices
✅ Use reputable, updated antivirus & EDR solutions
✅ Enable real-time protection & behavior monitoring
✅ Avoid cracked software and suspicious downloads
✅ Use hardware wallets for crypto assets
✅ Enable 2FA everywhere
✅ Keep Windows and browsers fully updated
Signs of Possible Infection
- Sudden account logouts
- Unauthorized crypto transactions
- Antivirus being disabled automatically
- Unknown background processes
If suspected, disconnect from the internet immediately and run a full system scan.
Download AVM Stealer 2026
Final Thoughts
AVM Stealer 2026 represents the evolution of infostealer malware, emphasizing stealth, automation, and broad data targeting. While attackers continue to innovate, awareness and proactive security hygiene remain the strongest defense.
Staying informed is not optional in 2026—it’s essential.