Pulsar RAT 2026
Key Capabilities Discussed in Pulsar RAT 2026 (Cybersecurity Analysis)
Security researchers analyzing Pulsar RAT 2026–style threats often highlight a range of capabilities that explain why modern Remote Access Trojans (RATs) remain a serious concern for individuals and organizations across the US and UK. Understanding these features helps defenders recognize risks and improve prevention strategies.
⚠️ The following overview is for educational and threat-awareness purposes only.
Improved Connectivity and Stability
Modern RAT variants emphasize faster and more stable remote connections. This allows attackers to maintain persistent access with fewer interruptions, making detection more difficult for traditional security tools.
Enhanced Remote Desktop Performance
Advanced remote desktop functionality may include smoother screen rendering and higher frame rates, sometimes leveraging GPU acceleration technologies. From a defensive standpoint, this means compromised systems can be controlled in near real time, increasing potential damage.
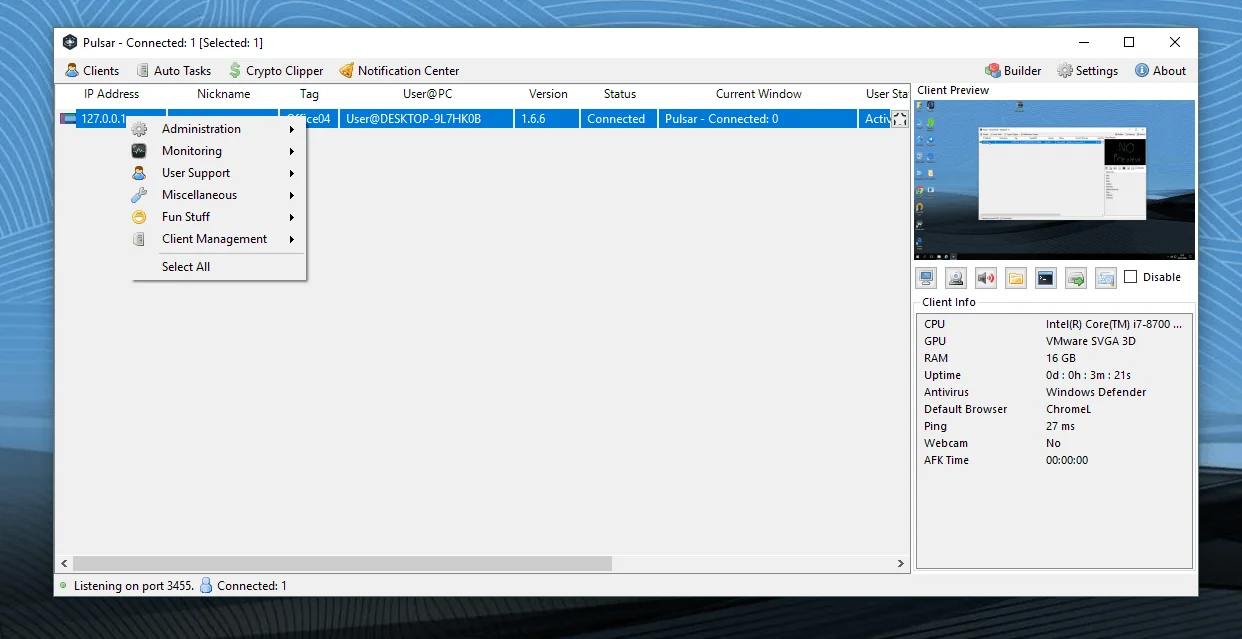
Instant Client Preview
Some RAT threats provide a preview of a compromised system’s desktop along with basic system information. This enables attackers to quickly assess the value of a target, which is why endpoint monitoring and access controls are critical.
Hidden VNC (hVNC) Capabilities
Hidden VNC techniques allow attackers to interact with browsers and applications in a concealed environment that the user cannot see. Compatibility with multiple browsers increases the risk of credential theft and session hijacking, particularly in online banking and cloud services.
Information-Stealing Components of Pulsar RAT 2026
Data-stealing modules are among the most dangerous features. These may target:
- Stored browser credentials
- Cookies and active login sessions
- Cryptocurrency wallets
- Gaming or application session data
Such capabilities pose serious privacy and financial risks to users.
Microphone Monitoring Risks
Some RATs can access a device’s microphone, potentially enabling real-time audio surveillance. This highlights the importance of operating system permissions, endpoint protection, and hardware access alerts.
Cryptocurrency Address Manipulation
Crypto address replacement techniques are designed to intercept copied wallet addresses and swap them with attacker-controlled ones. This threat has become increasingly relevant in regions with high crypto adoption, including the US and UK.
Virtual or Invisible Display Environments
Virtual monitor functionality allows attackers to operate within an unseen desktop environment. Because the victim may not notice visible screen activity, such attacks can persist longer without detection.
Memory Extraction Techniques
Memory dumping capabilities enable attackers to extract sensitive data from active processes, potentially bypassing encryption or security protections. This is a major concern for enterprises handling credentials or proprietary data.
Disruptive or Psychological Tactics
Some threats include disruptive actions such as interface manipulation or forced system crashes. While sometimes described as “pranks,” these behaviors can cause data loss, downtime, and user distress.
On-Screen Interaction
The ability to draw or interact directly with a victim’s screen during a remote session can be used for intimidation, social engineering, or manipulation—further increasing the impact of an attack.
Persistence Beyond System Resets
One of the most alarming characteristics discussed by analysts is persistence. Certain RAT threats may survive standard system resets, including cloud-based resets, making professional remediation or full system reinstallation necessary.
Why These Features Matter for US & UK Users
For users and businesses in the US and UK, these capabilities underline the importance of:
- Advanced endpoint detection and response (EDR)
- Regular software and OS updates
- Strong email and download hygiene
- User education against phishing and social engineering
- Network-level monitoring and firewalls
Download Pulsar RAT 2026
Final Security Perspective about Pulsar RAT 2026
The features associated with Pulsar RAT 2026 illustrate how sophisticated modern malware has become. While attackers focus on stealth and persistence, defenders must prioritize awareness, layered security, and rapid incident response.
Understanding how these threats operate—without engaging in misuse—is a key step toward a safer digital environment.